Creating a Google Cloud Platform service account key
Some context… A service account is a special type of Google account intended to represent a non-human user that needs to authenticate and be authorized to access data in Google APIs.
Lately I have been helping customers that are using CDAP, an 100% open source, integrated framework that accelerates application development for data analytics. Specifically around creating and connecting to Google Cloud Storage as a source to ingest and do data preparation (a.k.a data wrangling). The following post demonstrates how to create an API key file that can be used for any type of application that requires connectivity to Google APIs.
An important note. A little over a year ago, Google acquired Cask Data (creator of CDAP) » fast forward to which Google recently unveiled a cloud native data integration and ETL service called Cloud Data Fusion. More on that in future posts… ;-)
Let’s do this!
Log on to the GCP console
Go to the GCP console and log in using your Google account
Selecting a GCP project
You need to select a project. If you don’t have any projects then go to the project selector page to create one - For this demonstration I have created and using a specific project named cdap-gcs.
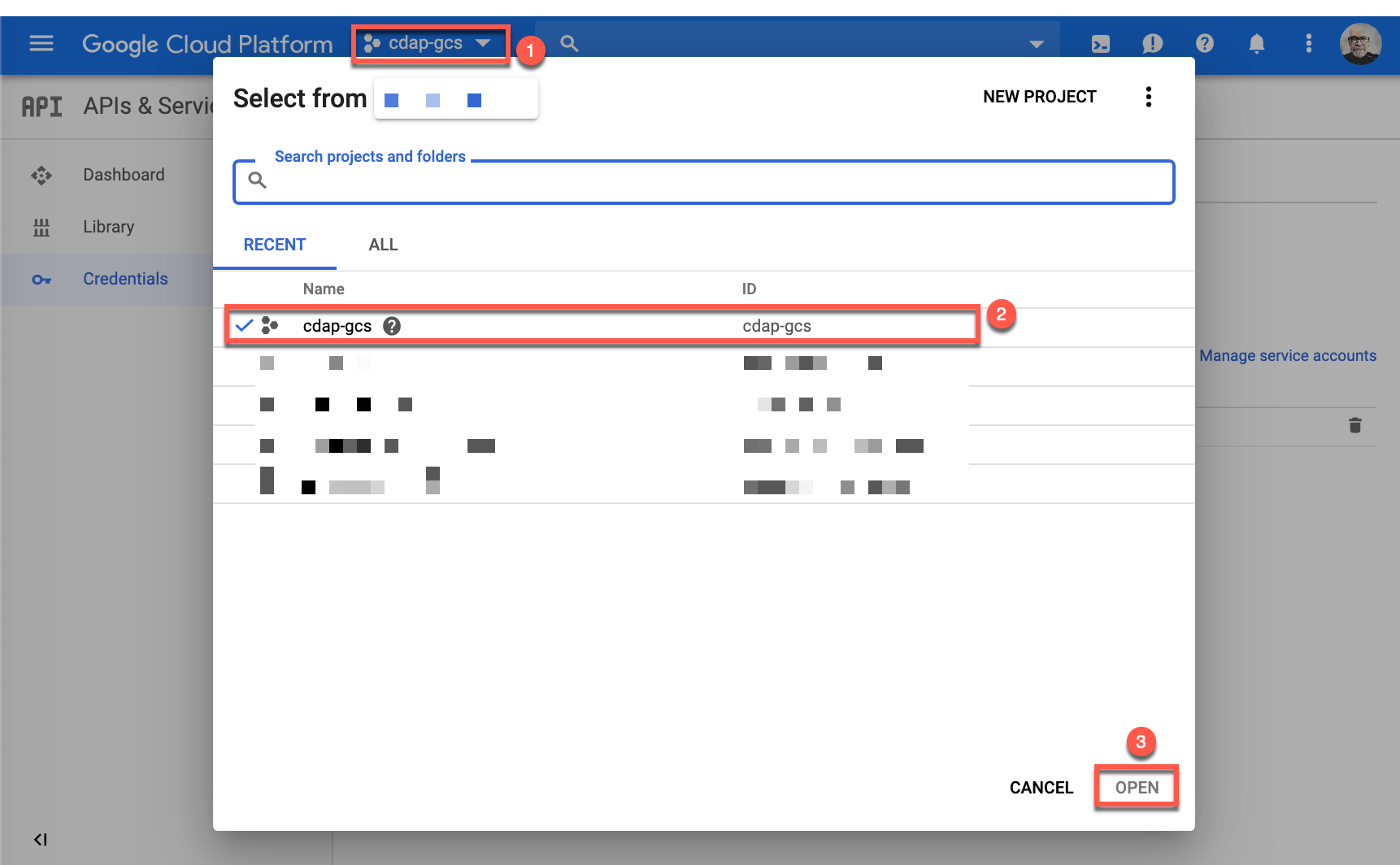
If the GCP project you want to use is not the one shown or selected, click the project name (1), then select the name of the GCP project you want to use (2), and click on Open (3).
Creating a GCP service account key
In this section you create a GCP service account key
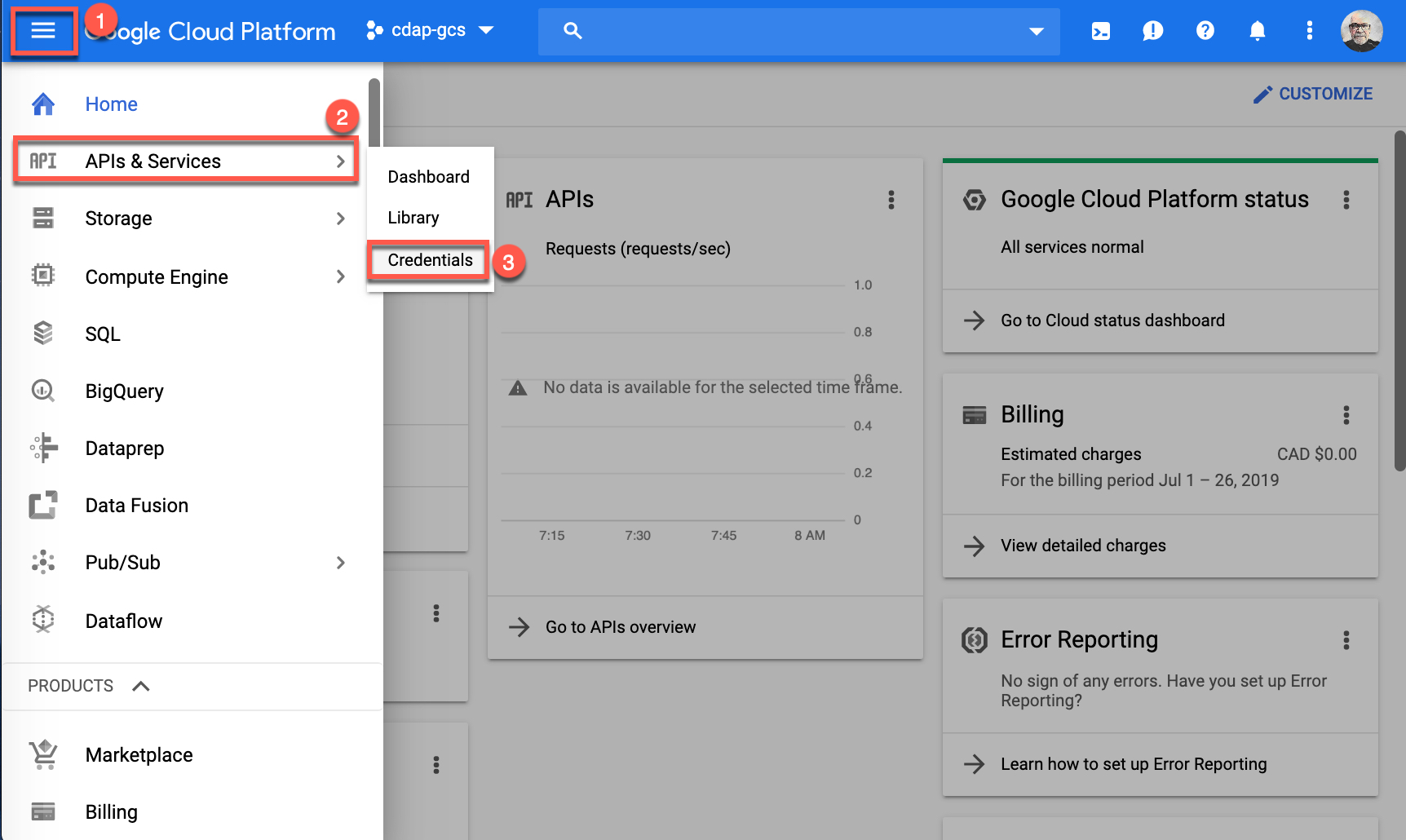
Select menu icon at the top of the screen (1), hover your cursor over APIs & Services (2), and select Credentials (3).
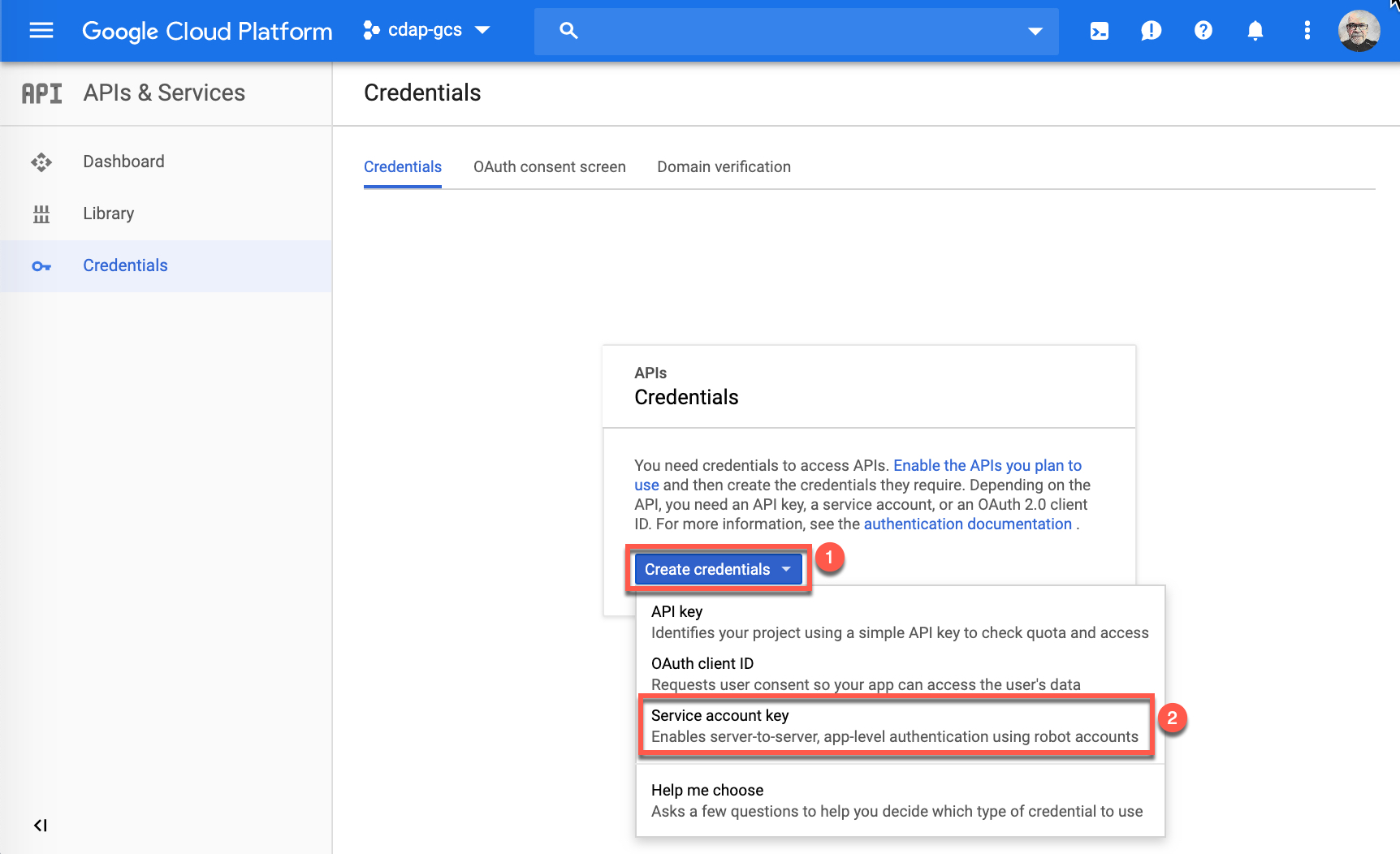
This brings you to the Credentials page. Click on the Create credentials (1) and hover your cursor over Service account key (2) and click.
Next follow these steps to create a service account key:
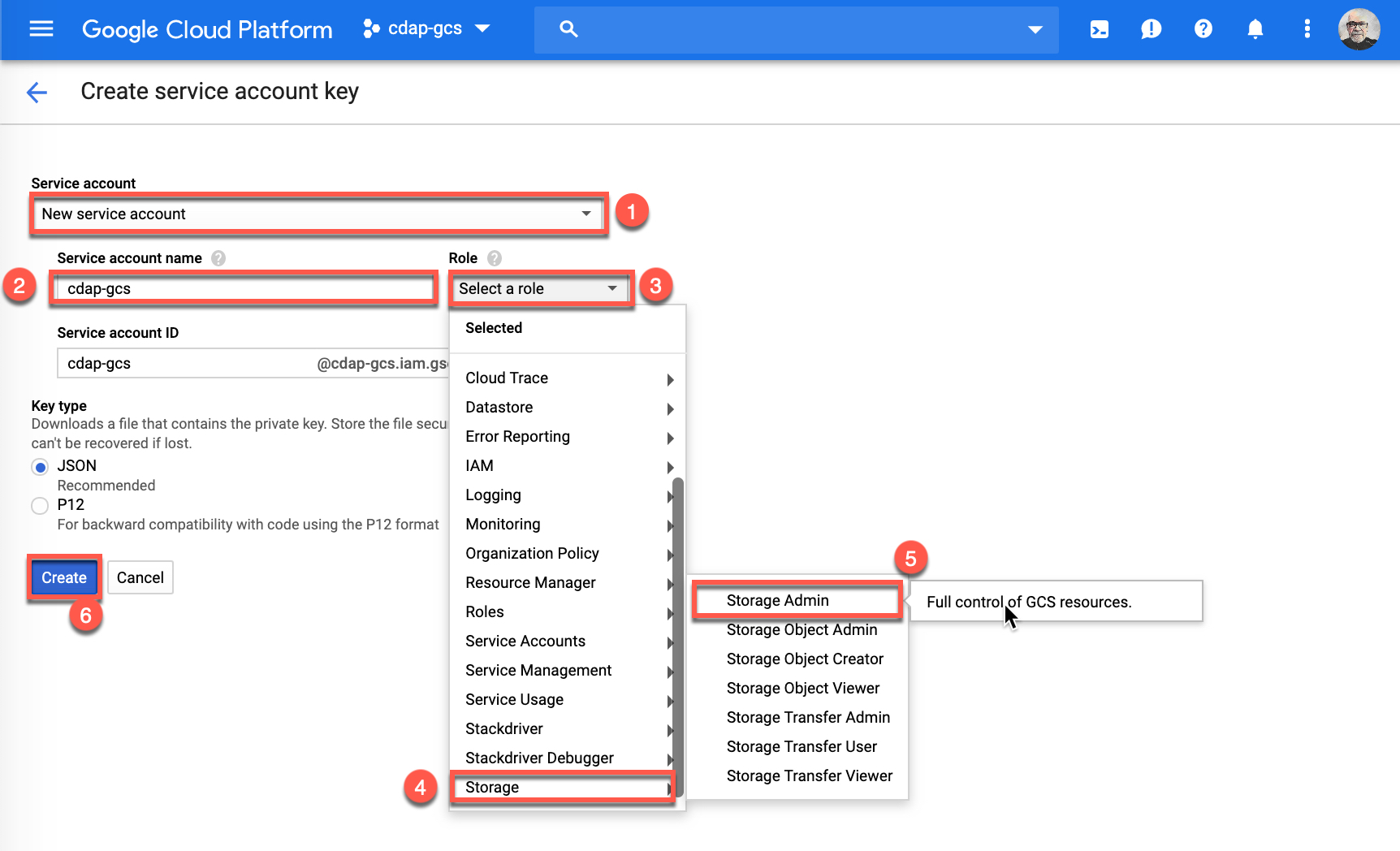
- Select New service account
- Enter a name for the Service account name
- Click on Select a role.
- Hover your cursor over to Storage.
- And select Storage Admin.
- Then click Create to download your key file.
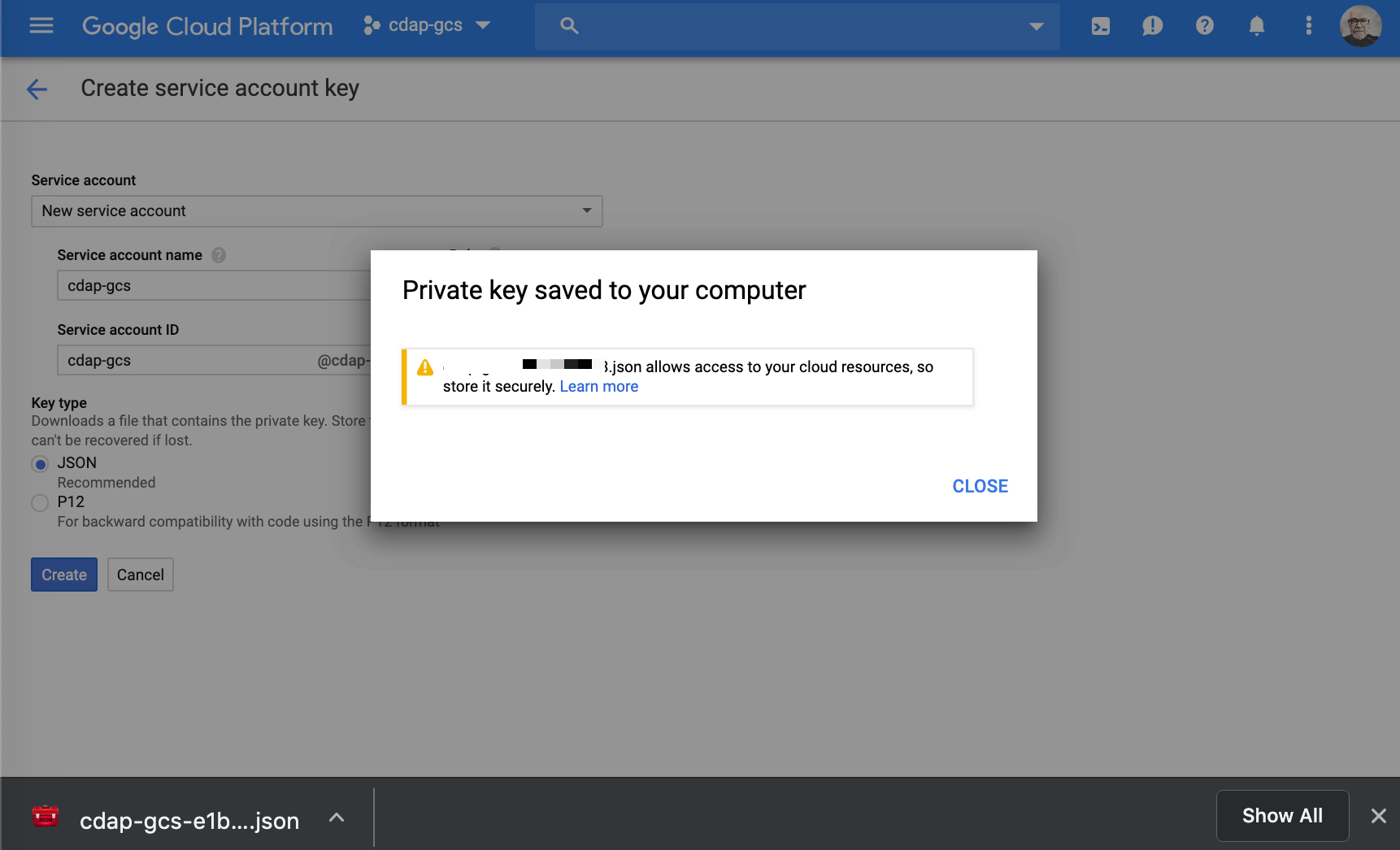
A confirmation will display that your service account key was downloaded. It is best practices to store your keys in a safe and secure location on your computer!
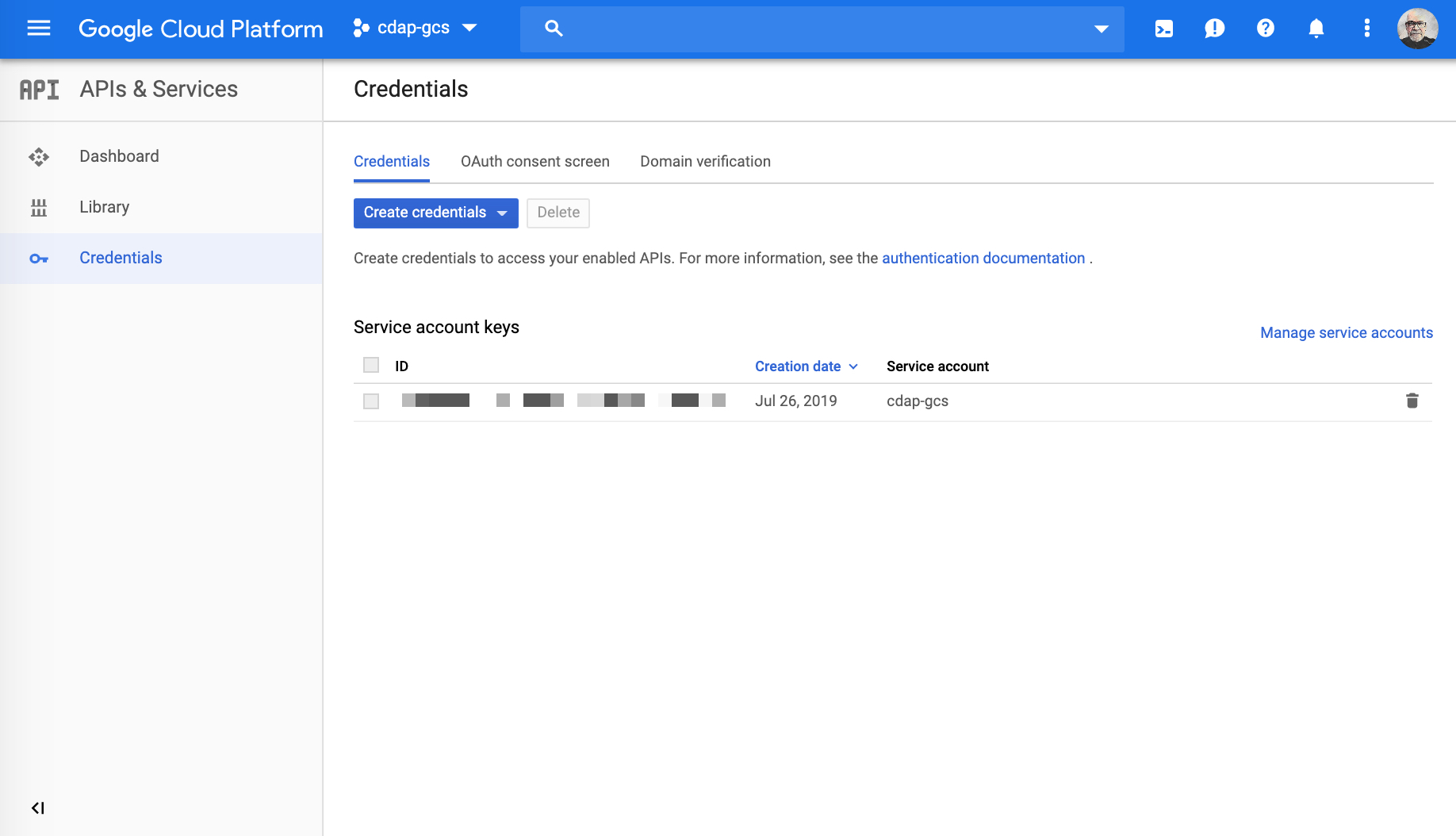
You now can view a list of your service account keys from the Credentials menu item.
With that, you have successfully created a GCP service account key. You will need to register the service account file you downloaded into the application to connect to GCP services.
Using the gcloud command
Now let’s see how you would do the same thing, but from the command line interface using gcloud commands.
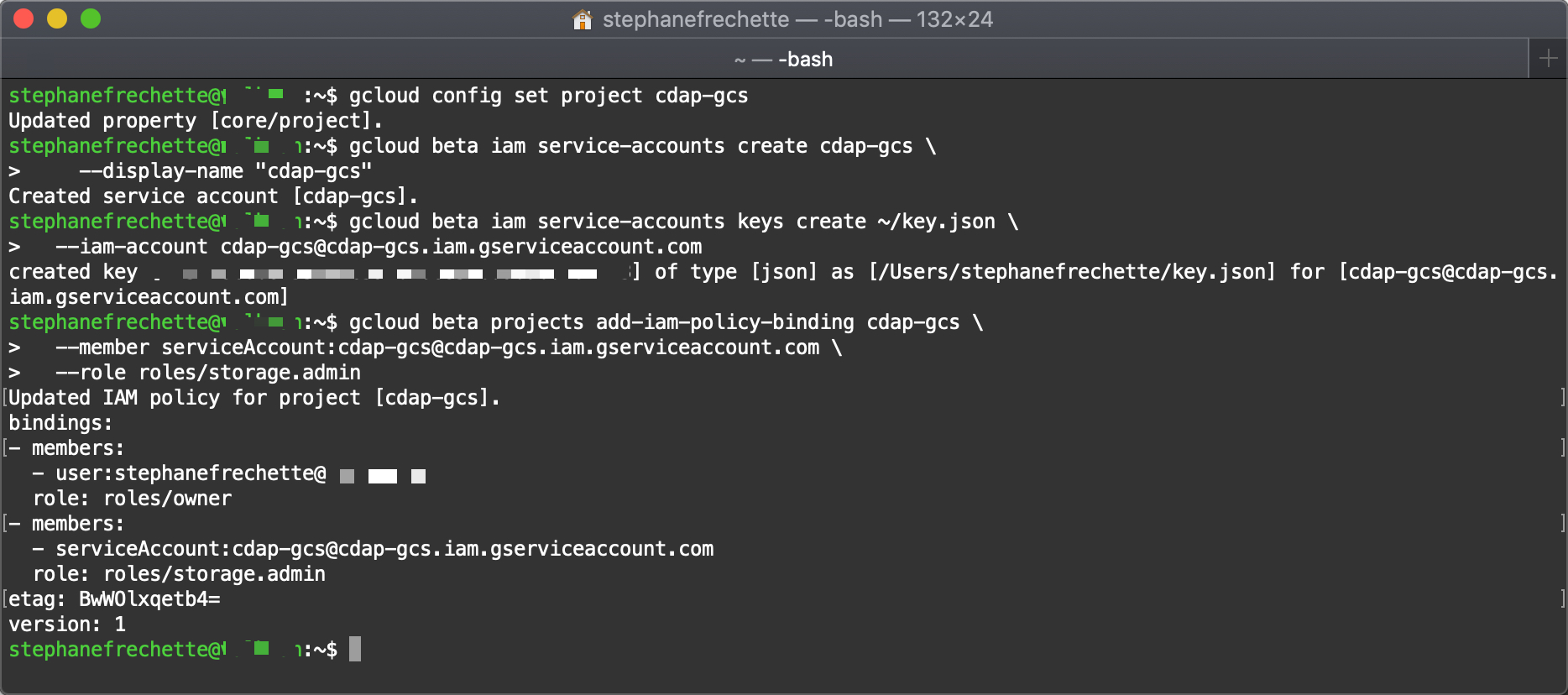
First let’s make sure you are setting and using to the right project. In this demonstration I am setting it to the cdap-gcs project I already created.
Reference: https://cloud.google.com/sdk/gcloud/reference/config/set
gcloud config set project cdap-gcs
Next you create a service account named cdap-gcs.
Reference: https://cloud.google.com/iam/docs/creating-managing-service-accounts
gcloud beta iam service-accounts create cdap-gcs \
--display-name "cdap-gcs"
Then create a service account key, in this demonstration named key.json using the IAM service account you just created cdap-gcs@cdap-gcs.iam.gserviceaccount.com.
Reference: https://cloud.google.com/sdk/gcloud/reference/iam/service-accounts/keys/create
gcloud beta iam service-accounts keys create ~/key.json \
--iam-account cdap-gcs@cdap-gcs.iam.gserviceaccount.com
And finally you add an IAM policy binding with the roles/storage.admin role to the service account member. cdap-gcs@cdap-gcs.iam.gserviceaccount.com
Reference: https://cloud.google.com/sdk/gcloud/reference/beta/projects/add-iam-policy-binding
gcloud beta projects add-iam-policy-binding cdap-gcs \
--member serviceAccount:cdap-gcs@cdap-gcs.iam.gserviceaccount.com \
--role roles/storage.admin
Output
That’s it! You’ve just created a GCP service account key.
Enjoy!